Monday, December 26, 2011
Classification of Programming Languages
Non-scripting languages (C, C++, C#, VB.NET, Java)
Types of Programming Languages
Job control languages and shells
Unix shell / MS-DOS COMMAND.COM/ Apple Script
GUI scripting
automate multiple user actions - "macros" / OS dependent
Application-specific languages
QuakeC, Emacs Lisp
Web browser based
JavaScript; VBScript , XSLT (XML), AJAX
Text processing languages
Unix (AWK, sed, grep)
General-purpose dynamic languages
TCL/ Python, Perl
Extension/embeddable languages
Action Script, python for GIMP , Adobe Acrobat (for scripting PDF files).
Python for Blender
http://en.wikipedia.org/wiki/List_of_programming_languages
Tuesday, December 13, 2011
Solid State Hard Drives
Basic components of a typical solid-state hard drive.
Solid staed drives are made up of many SDRAM modules stacked on an array with a the supporting battery. They are very fast but the price is high. They are used in PCMCIA cards, flash cards, etc. Solid state hard drives are made up entirely of RAM modules. It uses standard SDRAM modules to store information. SDRAM is volatile memory. it loses its information when there is no power. A rechargeable lithium-ion battery used to provide power when AC power is unavailable.
A high-end magnatic hard drive has an I/O rate of about 60 to 90 IO s/sec. A solid-state disk in comparison can range from 5000 to 9000 IO s/sec. A high-end conventional hard drive has an average access time of 6 to 8 milliseconds. A solid-state disk in comparison has an average access time of 50 to 100 microseconds. Applications like video editing and mission critical issues can take advantage of the speed benefits.
Some Interesting Hardware Articles
Sunday, December 11, 2011
Boolean Logic, Truth Tables and Karnaugh Maps
- Boolean Algebra #1
- Boolean algebra #2: Basic problems
- Boolean algebra #3: Basic problems
- Boolean algebra #4: Different terminology and notations
- Boolean algebra #5: Truth tables - introduction
- Boolean algebra #6: Truth tables - variables combinations
- Boolean algebra #7: Truth tables - example problems
- Boolean algebra #8: Truth tables - into expressions/statements
- Boolean algebra #9: truth tables - into expressions (continued)
- Boolean algebra #10: Truth tables - example
- Boolean algebra #11: Truth tables - example (continued)
- Boolean algebra #12: Karnaugh maps
- Boolean algebra #13: Karnaugh maps example (continued)
- Boolean algebra #14: Karnaugh maps - short summary
- Boolean algebra #15: Karnaugh maps - from expressions
- Boolean algebra #16: Karnaugh maps - from expressions (continued)
- Boolean algebra #17: Karnaugh maps - grouping
- Boolean algebra #18: Karnaugh maps - grouping (continued)
- Boolean algebra #19: Karnaugh maps - getting the result
- Boolean algebra #20: Karnaugh maps - getting the result (continued)
- Boolean algebra #21: Karnaugh maps - getting the result (continued)
- Boolean algebra #22: Karnaugh maps - final example
- Boolean algebra #23: DeMorgan's theorem - introduction
- Boolean algebra #24: DeMorgan's theorem - examples
Boolean algebra #25: DeMorgan's theorem - examples (continued)- Boolean algebra #26: Sum of products (SOP) form
- Boolean algebra #27: Standard SOP form
- Boolean algebra #28: Standard SOP form (continued)
- Boolean algebra #29: Product of sums (POS) form
- Boolean algebra #30: Product of sums (POS) form (continued) Web Tutorials
- Karnaugh Maps 1
- Karnaugh Maps 2
- Karnaugh Maps 3
Boundedness Law
Minterms and Maxterms
Any boolean expression may be expressed in terms of either minterms or maxterms.
Literal
A literal is a single variable within a term which may or may not be complemented.
A minterm is the product of N distinct literals where each literal occurs exactly once.
A maxterm is the sum of N distinct literals where each literal occurs exactly once.
The minterms and maxterms for a two-variable expression is
A B Minterm Maxterm
0 0 A'.B' A+B
0 1 A'.B A+B'
1 0 A.B' A'+B
1 1 A.B A'+B'
The minterms and maxterms for a three variable expression is
A B C Minterm Maxterm
0 0 0 A'.B'.C' A+B+C
0 0 1 A'.B'.C A+B+C'
0 1 0 A'.B.C' A+B'+C
0 1 1 A'.B.C A+B'+C'
1 0 0 A.B'.C' A'+B+C
1 0 1 A.B'.C A'+B+C'
1 1 0 A.B.C' A'+B'+C
1 1 1 A.B.C A'+B'+C'
Saturday, December 10, 2011
Thursday, December 8, 2011
ඔබ සයිබර් ත්රස්තවාදය ගැන අහල තිබෙනවද?

අද අප ඔබට කියන්නට යන්නේ රුසියාවෙන් වාර්තා වූ සයිබර් ත්රස්තයන් කිහිප දෙනෙකු ගැනයි. ඔවුන් රුසියවේ සිට ඇමරිකාවේ ජලසම්පාදන දෙපාර්තමේන්තුවේ වෙබ් අඩවිවලට රිංගලා එරට ඉලිනොයි ප්රාන්තයේ ජල සැපයුම අඩාල කළා. ඇමරිකාව, බ්රිතාන්යය, ජර්මනිය, ප්රංශය වැනි රටවල ජලසම්පාදනය සහ ජලාපවහනය පාලනය කෙරෙන්නේ පරිගණක තාක්ෂණයෙන්. මෙවැනි පරිගණක පද්ධතියක වැඩසටහනක් ඉන්ටර්නෙට් හරහා අවුල් කළ විට කළ හැකි හානිය අපමණයි. අඩු පීඩනයක් දැරිය හැකි ජල නල වෙත වැඩි පීඩනයක් සහිත ජල තොග මුදාහරිමින් එම ජලනල පිපිරවීම පවා කළ හැකියි.
රුසියන් සයිබර් ත්රස්තයන් පිරිසත් ඒ වගේ වැඩක් කළා. ඔවුන් වැරදි විධාන ලබාදී ඉලිනොයි ප්රාන්තයේ ජල පොම්පයක් සම්පූර්ණයෙන්ම විනාශ කළා. මේ නිසා නිවාස දහස් ගණනකට ජලය නැති වුණා. ස්ප්රිංෆිල්ඩ් නගරයට වතුර සපයන පොම්පය ඔවුන් කැඩුවේ පොම්පය අරින වහන ලෙස කඩින් කඩ නියෝග නිකුත් කිරීමෙන්. මෙය සිදු වූයේ පසුගිය (නොවැම්බර්) 8 වැනිදා.
මෙහි තත්ත්වය වඩාත් බරපතල වූයේ කම්පියුටර් හැකර් කෙනෙක් හෙවත් අනවසරයෙන් වෙබ් අඩවිවලට රිංගන තවත් පුද්ගලයෙක් ඇමරිකන් ආරක්ෂක පද්ධතියේ බලය තමන් අතට පත්වූ බව වාර්තා කිරිමෙන්. මෙය ඉතා භයානක වැඩක්. ඔහු ඇත්තටම එබන්දක් කර තිබුණා නම් විනඩි කිහිපයක් තුළ ඇමරිකන් මිසයිල පද්ධතිය පරිගණක හරහා ක්රියාත්මක කර තුන්වන ලෝක යුද්ධය ඇතිකරන්නට ඔහුට හැකි වනවා.
ඇමරිකාවෙන් පිටත සිට ඇමරිකාවේ යටිතල පහසුකමක් පරිගණක හරහා කඩාකප්පල් කළ පළමු අවස්ථාව මෙය බවයි වාර්තා වෙන්නේ. පරිගණක පද්ධති හැකර්ලාගෙන් බේරා ගැනීම සඳහා උපදෙස් දෙන ඇමරිකන් උපදේශකයකු වන ජෝ වෙඩිස් කියන්නේ හැකර්ලා මේ තරම් බලවත් වීම තුළ ඉමහත් තර්ජනයක් හටගෙන ඇති බවයි. මේ ගැන ඇමරිකන් ෆෙඩරල් බියුරෝවත් ස්වදේශාරක්ෂක දෙපාර්තමේන්තුවත් පරීක්ෂණ පවත්වනවා.
සයිබර් ත්රස්තයන් අතට ඇමරිකන් ජල දෙපාර්තමේන්තුවේ පාස්වර්ඩ් ගියේ කොහොමද? ඒ පරිගණක පද්ධතියට ලොග් වෙන හැටි ඔවුන් දැනගත්තේ කොහොමද? විවිධ පාස්වර්ඩ් ලක්ෂ ගණනක් යෙදීමෙන් පසු එයින් එකක් අහඹු ලෙස හරියන්නට පුලුවන් බව සමහරුන්ගේ මතයයි. ඒත් හරියටම ඒ පාස්වර්ඩ් රටාව ඔවුන් අල්ලාගත්තේ කොහොමද කියන එකයි ප්රශ්නය.
මේ පාස්වර්ඩ් නිර්මාණය කරන්නේ ලොව පුරා ඇති සංවේදී කර්මාන්තශාලා (යුද අවි, ගුවන් යානා, රසායනික ද්රව්ය, ඖෂධ) සඳහා පරිගණක මෘදුකාංග සාදන ඇමරිකාවේ ඇප්ලයිඩ් කන්ට්රොaල් සොලියුෂන්ස් ආයතනයයි. න්යෂ්ටික බලාගාරවලටත් තෙල් ළිං වලටත් මේ සමාගම මෘදුකාංග හදනවා.
පුපුරුවා හරින ලද වතුර පොම්පය කැඩුනේ ටිකෙන් ටික. එය දිනකට නියමිත ප්රමාණයට වඩා අරිමින් සහ වසමින් තිබුණා. පොම්ප පද්ධතිය ඇත්තේ ආවරණය කළ අධි ආරක්ෂක කුටියක් තුළ නිසා එය කැඩෙමින් පවතින බව කවුරුවත් දැන සිටියේ නැහැ.
ඇමරිකාවේ මෙබඳු ස්වයංක්රීය ජලාපවාහන පද්ධති මිසයිල පද්ධති යනාදිය සඳහා මෘදුකාංග නිපදවන පෙර කී සමාගම එම මෘදුකාංගයට කියන්නේ Supervisory
Control and Data Acqnisition හෙවත් “ස්කාඩා” කියලයි. මේ මෘදුකාංගය හරහා පරිගණක පද්ධතියට ඇතුළත් වීමට හැකර්ලාට බැරි බවයි මෙතෙක් කල් හිතාගෙන හිටියේ. ඒ නිසාම එයට පිවිසෙන හැකර්ලා පිළිබඳ සාක්ෂි සොයන වැඩපිළිවෙළකුත් තිබුණේ නෑ. ස්කාඩා මෘදුකාංගය හදන සමාගමේ ප්රකාශක පීටර් බුගාර්ඩ් පසුගියදා ප්රකාශ කළා වතුර පොම්පයක් කඩනවාට වැඩි යමක් කරන්නට හැකර්ලාට බැරි බව. ඒ එක්ක Prof යනුවෙන් පෙනී සිටි හැකර් කෙනෙක් ඊමේල් හරහා ප්රකාශ කළා තමන් ටෙක්සාස් ප්රාන්තයේ දකුණු හුස්ටන් නගරයේ යටිතල පහසුකම් පද්ධතියක පාස් වර්ඩ්එක සොයාගත් බව. මෙය අප ජලය පිරිසිදු කරන පද්ධතියක්.
ස්කාඩා මෘදුකාංග පද්ධතියේ පාස් වර්ඩ් එකට තිබෙන්නේ අකුරු ඉලක්කම් හෝ සලකුණු තුනක් පමණක් බව එම හැකර් ප්රකාශ කිරීමෙන් ඔහු ඒ ගැන ඉතා හොඳින් දන්නා බව ඔප්පු වුණා. ඊටත් අමතරව ඔහු එම වතුර පිරිපහදු යන්ත්රාගාරයේ පරිගණක ක්රියාකාරිත්වයට අදාළ ලින්ක් හෙවත් සම්බන්ධ විය හැකි ක්රම කිහිපයකුත් ප්රකාශ කර තිබුණා.
ස්කාඩා පද්ධතිය සයිබර් ත්රස්තවාදයෙන් බේරා ගැනීම ගැන විද්යාඥයන්ට අලුතින්ම හිතන්නට වී තිබෙනවා. මන්දයත් පසුගිය වසරේදී ඉරානයේ යුරේනියම් සැකසුම් මධ්යස්ථානයේ පරිගණක මෘදුකාංග පද්ධතියට (එහි කේන්ද්රානුසාරකය හෙවත් Centrifuge එකට) Stuxnet නමින් හැඳින්වුණු වෛරස් ප්රහාරයක් එල්ල වීම නිසයි. යුරේනියම් යනු පරමාණු බෝම්බ සෑදීමට හැකි ද්රව්යයක්. න්යෂ්ටික බලාගාර ක්රියාත්මක කරන්නටත් යුරේනියම්වලට පුලුවන්. එවැනි දෙයක් සකසන තැනකට සයිබර් ප්රහාරයක් එල්ල වීම සෙල්ලමක් නොවෙයි. මේ ප්රහාරය නිසා තම න්යෂ්ටික වැඩපිළිවෙළ ආපස්සට ගන්නට ඉරානයට සිදු වුණා. සමහරුන් කියන්නේ මේ වෛරස් ප්රහාරයට වගකිව යුත්තා ඇමරිකානු හෝ ඊශ්රායල හැකර් කෙනකු බවයි.
ඇමරිකාවේ විදුලිබල බෙදාහැරීම ඉතාම පැරණි අබලන් එකක්. වසර 2007 දී සිදුවූ විදුලි බිඳවැටීමක් සති දෙකක පමණ කාලයක් පැවතුණා. එය ශීත Rතුවක්. විදුලි බලය නැතිව නිවාස උණුසුම් කරගැනීමට බැරිව ඇතැම් ඇමරිකානුවන් මිය ගියා. එසේ තිබියදී ඩීසල් බලාගාරයකට සයිබර් ප්රහාරයක් එල්ල වුණොත් කොතැනින් නවතීද කියන්න බෑ. සමහර විට තුන්වන ලෝක යුද්ධය මෙබඳු සයිබර් ප්රහාරයකින් පටන් ගන්නටත් පුලුවන්. එය සිදුවන්නේ මෙහෙමයි. හැකර් කෙනකුට පුලුවන් ඇමරිකන් න්යෂ්ටික මිසයිල අංගනයක පාස් වර්ඩ් එක සොයාගෙන ඒ හරහා “කමාන්ඩ් එකක්” එවා රුසියාවට පහර දෙන්නට රුසියාවත් එවිට ප්රති ප්රහාර දෙනු ඇති ඊළඟට ඒ රටවල් දෙකට සහය පිණිස දෙකෙට බෙදෙන ලෝක ජාතීන් මරා ගන්නට පටන් ගනීවි.
- අනුර සොලමන්ස් / දිවයින
Tuesday, December 6, 2011
FREE Online Webinar Services
Vyew
Dim Dim
YuuGuu
Tuesday, November 22, 2011
How to avoid worst passwords in online security
1. password
2. 123456
3. 12345678
4. qwerty
5. abc123
6. monkey
7. 1234567
8. letmein
9. trustno1
10. dragon
11. baseball
12. 111111
13. iloveyou
14. master
15. sunshine
16. ashley
17. bailey
18. passwOrd
19. shadow
20. 123123
21. 654321
22. superman
23. qazwsx
24. michael
25. football
26. abc
27. goodboy
28. userid
29. userid1
Here are some tips to have strong passwords
1.Strong Master Password
Create a strong master password for your main email
2.Randomize Passwords
Use random passwords for websites with lengths of 15-20 . if you dont use them always, you can ask to send password to your master email.
2. Protect your master account. Never keept it's password on phone or your text book. Keep it in your mind and safe at home.
4. Dont reuse passwords in different accounts.
5.User IDs
Consider randomizing your username depending on what you are protecting. Never use your online banking user id anywhere.
5.Secret Qusetion
Your friends and relatives knows answers to default questions given by google and yahoo. Create your own privcy. What was my favorite food, drink when I was ill? combine information in a question. And make it random.
Username: 88N1iRQ1o9XM1Xi#4KLs
Password: [yBNSkG%/8r!:[g8O9N6
and
Use unicode characters from other languages
Use slangs from your own locality
Never use anything in dictionaries
Never use 123 or abc anywhere
Dont keep your passwords only in memory, have a recovery mechanism
Privacy Guide on Facebook
Privacy SettingsOnce logged into your account on Facebook,
Goto Account> Privacy Settings
1.Everyone - public with no restriction be carefull with this option
2.Friends of Friends - tricky , your friends may have fake friends
3.Friends Only - Make sure you know them and not fake ones
Account > Privacy Settings > Customize Settings > Things I Share
Pay a special attention to "Posts by me"
Account > Privacy Settings > Customize Settings > Things Others Share
What you actually want to see, make sure you don't waste your time
Account > Privacy Settings > Customize Settings > Contact Information
Omit your Email Address and Phone Number
Account > Privacy Settings > Customize Settings > Things I Share > Posts by Me
Select "Custom" and set your privacy requirement
Account > Privacy Settings > Customize Settings > Things Others Share > Photos and videos you're tagged in
Account > Privacy Settings > Customize Settings > Things Others Share > Suggest photos of me to friends
Account > Privacy Settings > Customize Settings > Things Others Share > Friends can check me in to Places
Account > Privacy Settings > Customize Settings > Things I Share > Edit privacy settings for existing photo albums and videos
Account > Privacy Settings > Apps, Games and Websites
Account > Account Settings > Account Security
Account > Account Settings > Facebook Ads
Edit my Profile
My Wall
Public Directory
1. Don't assuem that your virus guard to protect you 100%.
2. Don't Accessing an account through an e-mail link to provide sensitive information.
Criminals using “phishing” scams use emails to steal your logins, account numbers and other sensitive data. The web you use would look like genunie with same design and have a url like somedomain.com/facebook or even facebook1.com to disguise.
They look legitimate to users who are busy. "it’s pretty much impossible for people to know … if the e-mail is real or not" says an expert.
3. Use multiple passwords
If you use one password for all accounts and If somebody manages to get hold of your password … they will have entry into all your accounts and impersonate you.
4. Downloading free software
Free software is good. Only download software from places you know are safe like sourceforge, cnet etc. Some “free” software comes loaded with spyware. They hijack your browser, port 80 and employs keystroke-capture programz to steal your personal data.
5. don't Click on pop-up ad that says your PC is not secure
They take you to spyware sites or have malicious software downloaded to your computer.
Instead, click on the tiny “close” button in the right corner. Best is to enable your browser’s pop-up blocker.
6. Don't use debt cards to Shop online
Use a separate card for your online purchases. Don’t shop online with debit cards, if stolen they offer no liability protection.
7. https and httpMake sure when you are entering your address and credit card information, that the site’s URL says “https”. https offers greater security than “http.”
Saturday, November 19, 2011
OSI (Open Systems Interconnect) Model Animation
 For example, a layer that provides error-free communications across a network provides the path needed by applications above it, while it calls the next lower layer to send and receive packets that make up the contents of that path.
For example, a layer that provides error-free communications across a network provides the path needed by applications above it, while it calls the next lower layer to send and receive packets that make up the contents of that path.Layer 1: Physical layer
defines electrical and physical specifications for devices.
defines the relationship between a device and a transmission medium, such as a copper or optical cable, including the layout of pins, voltages, cable specifications, hubs, repeaters, network adapters and more.
Establishment and termination of a connection to a communications medium.
Sharing communication resources effectively among multiple users.
Modulation (conversion from and to digital)
Layer 2: data link layer
Provides the functional and procedural means to transfer data between network entities and to detect and possibly correct errors that may occur in the physical layer.
IEEE 802.3 dominant wired LAN protocol (ETHERNET)
IEEE 802.11 the wireless LAN protocol
Layer 3: network layer
Provides the functional and procedural means of transferring variable length data sequences from a source host on one network to a destination host on a different network.
Performs network routing functions, and might also perform fragmentation and reassembly, and report delivery errors. Routers operate at this layer, sending data throughout the extended network and making the Internet possible.
Layer 4: transport layer
Provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers. The transport layer controls the reliability of a given link through flow control, segmentation/desegmentation, and error control. Some protocols are state- and connection-oriented. This means that the transport layer can keep track of the segments and retransmit those that fail. The transport layer also provides the acknowledgement of the successful data transmission and sends the next data if no errors occurred.
Transport layer is like a Post Office, which deals with the dispatch and classification of mail and parcels sent. The post office manages the outer envelope of mail. Higher layers may have the equivalent of double envelopes, such as cryptographic presentation services that can be read by the addressee only.
The Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) of the Internet Protocol Suite are commonly categorized as layer-4 protocols within OSI.
Layer 5: session layer
Controls the dialogues (connections) between computers. It establishes, manages and terminates the connections between the local and remote application. It provides for full-duplex, half-duplex, or simplex operation, and establishes checkpointing, adjournment, termination, and restart procedures. The OSI model made this layer responsible for graceful close of sessions, which is a property of the Transmission Control Protocol, and also for session checkpointing and recovery, which is not usually used in the Internet Protocol Suite. The session layer is commonly implemented explicitly in application environments that use remote procedure calls.
Layer 6: presentation layer
Establishes context between application-layer entities, providing independence from data representation (e.g., encryption) by translating between application and network formats. The presentation layer transforms data into the form that the application accepts.
Converting an EBCDIC-coded text file to an ASCII-coded file, or serialization of objects and other data structures from and to XML.
Layer 7: application layer
The application layer is the OSI layer closest to the end user, which means that both the OSI application layer and the user interact directly with the software application. Application-layer functions typically include identifying communication partners, determining resource availability, and synchronizing communication. Synchronizes communication between applications requires cooperation that is managed by the application layer.
Some examples on TCP/IP stack:
- Hypertext Transfer Protocol (HTTP),
- File Transfer Protocol (FTP),
- Simple Mail Transfer Protocol (SMTP)
- Simple Network Management Protocol (SNMP).
Important Combinational Logic Circuits
An Algorithm to convert Decimal to any base
Friday, November 18, 2011
How Software agents work?
They can perform simple and repetitive tasks faster than human workers. They can be used for personal or commercial purposes, but can also be used in malicious attacks on users.
Google uses software agents (spiders/robots) to periodically visit web sites to index them in google search engine. An e commerce agent finds the best price for a phone model on e commerce sites
A Search engine Spider Simulator
Online chat agents search answers to keywords in a database to help users asking questions
A chatbot is a a computer program designed to simulate an intelligent conversation with human users.
Most chat bots simply scan for keywords within the input and pull a reply with the most matching answer from a database.
http://www.parnasse.com/drwww.shtml
search engines use robots to index web pages
Software agents (Bots) can be used to spread spam emails, viruses and scams.
Software Update Agents (Virus Guards)
How Googlebot Works ?
http://www.googleguide.com/google_works.html
Google's algorithm assigns a rank to each page based several factors,
1. how many times the keywords appear on the page.
2. Google looks for keywords in headings. K
3. Keywords in larger headings are more valuable than smaller headings
4. Google assigns a page rank every search result.
5. Search Position depends partially on number of other Web pages linking to target page. (vote)
6. Votes from a high-ranking Web page counts more
7. The more links a Web page sends out, the more diluted its voting power becomes.
Software Agents used in personalised information management, e commerce, interface design, computer games, and complex industrial processes. They are computer programs that can be delegated to do some tasks. They are mostly self-contained programs capable of controlling its own decision making and acting, based on its environment.
http://www.google.lk/search?q=software+agents&hl=en&biw=1366&bih=546&prmd=imvnsb&source=lnms&tbm=isch&ei=b6PGTu-sPMO4rAfKkuGoDg&sa=X&oi=mode_link&ct=mode&cd=2&ved=0CAsQ_AUoAQ
More :
Gopher agents:Execute straightforward tasks based on pre-specified rules and assumptions
- Inform when temperature rises by 10% from its mean position.
- Alert reorder stock items
Service performing agents
Execute a well defined task at the request of a user
- find the cheapest flight to Colombo
Predictive agentsProvides information or services to a user, without being asked
- monitor newsgroups on the INTERNET and return relevent discussions
• Autonomy: able to perform majority of tasks without direct human intervention and have a degree of control over their own actions and their own internal state.
• Social ability: able to interact, when appropriate, with other software agents and humans to solve problems
• Responsiveness: agents should understand their environment and respond to changes
• Proactiveness: agents takes automatic action where appropriate.
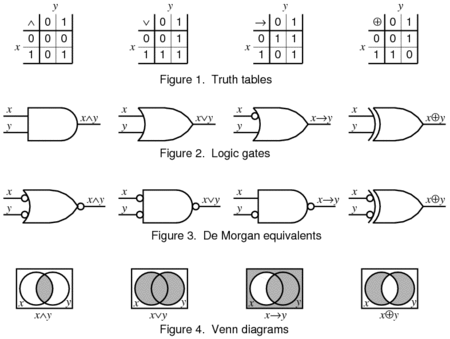
Boolean Algebra & Logic Gates for A/L ICT
Boolean Algebra & Logic Gates Start Up- Boolean Algebra & Logic Gates 1
- Boolean Algebra & Logic Gates 2 (From GIT Book)
- Simple Questions on Logic Gates
- Boolean Algebra & Logic Gates (Advanced)
- Logic Gates Revision (Simple)
Boolean algebra or Boolean logic is a calculation of truth values, developed by George Boole in the 1840s. In ICT it resembles logical multiplication xy, addition x + y, and negation −x to build combined circuits.
Boolean logic or Boolean algebra is a logical calculus which has only two values, 'true' or 'false'.
Boolean Logic is defined as a logical system of operators - 'AND', 'OR' and 'NOT'. It is a way of comparing individual bits and used in computer construction, switching circuits, etc.
' denotes negative
Boolean Algebra Quiz
1. Give the relationship that represents the dual of the Boolean property A + 1 = 1?
(Note: * = AND, + = OR and ' = NOT)
1. A * 1 = 1
2. A * 0 = 0
3. A + 0 = 0
4. A * A = A
5. A * 1 = 1
2. Give the best definition of a literal?
1. A Boolean variable
2. The complement of a Boolean variable
3. 1 or 2
4. A Boolean variable interpreted literally
5. The actual understanding of a Boolean variable
3. Simplify the Boolean expression (A+B+C)(D+E)' + (A+B+C)(D+E) and choose the best answer.
1. A + B + C
2. D + E
3. A'B'C'
4. D'E'
5. None of the above
4.Which of the following relationships represents the dual of the Boolean property x + x'y = x + y?
1. x'(x + y') = x'y'
2. x(x'y) = xy
3. x*x' + y = xy
4. x'(xy') = x'y'
5. x(x' + y) = xy
5.Given the function F(X,Y,Z) = XZ + Z(X'+ XY), the equivalent most simplified Boolean representation for F is:
1. Z + YZ
2. Z + XYZ
3. XZ
4. X + YZ
5. None of the above
6. Simplification of the Boolean expression (A + B)'(C + D + E)' + (A + B)' yields which of the following results?
1. A + B
2. A'B'
3. C + D + E
4. C'D'E'
5. A'B'C'D'E'
7. Given that F = A'B'+ C'+ D'+ E', which of the following represent the only correct expression for F'?
1. F'= A+B+C+D+E
2. F'= ABCDE
3. F'= AB(C+D+E)
4. F'= AB+C'+D'+E'
5. F'= (A+B)CDE
8. An equivalent representation for the Boolean expression A' + 1 is
1. A
2. A'
3. 1
4. 0
9. Simplification of the Boolean expression AB + ABC + ABCD + ABCDE + ABCDEF yields which of the following results?
1. ABCDEF
2. AB
3. AB + CD + EF
4. A + B + C + D + E + F
5. A + B(C+D(E+F))
Answers
1. A * 0 = 0. The dual of any Boolean property may be obtained by interchanging all occurrences of the symbols (*,+,0,1) with the symbols (+,*,1,0). Beware of implicit AND operations (like xy); these ANDs are also converted to +. Therefore, the dual of x + 1 = 1 is: x*0 = 0.
2. 1 or 2
3. A + B + C
4. x(x' + y) = xy
5. Z + XYZ
6. A'B'
7. (A+B)CDE (DeMorgan's theorem twice)
8. 1
9. AB
Sunday, November 13, 2011
AL ICT Binary, Hex, Ocal Numbers and Conversion Notes and Questions
Binary Numbers WorkSheet 2
Binary, Hex, Octal Number Systems and Conversions
Binary, Hex, Octal Number Systems Questions and Answers
2s Complement ....
More Binary Stuff....
They say that , there are 10 people in the world.
Those who know binary and those who don't.
Enjoy Binary ... The begining of ICT
Tuesday, November 8, 2011
How jQuery works and building Plug-ins
- 1) How jQuery works
A basic introduction to jQuery and the concepts that you need to know to use it.
- 2) jQuery For Designers
Examples of writing Unobtrusive
- JavaScript to add simple behaviour to a web page.
- 3) Building Your First jQuery Plug-in
This tutorial will take you step by step through creating your very own truncation plug-in.
- 4) How to display tips by creating a JQuery plug-in
We are going to learn how to create our custom jQuery plug-in to show tips on mouse over event on our desired elements. We will also be able to customize the appearance of the tip division for each kind of elements in the CSS code and much more.
- 5) Form validation with jQuery from scratch
The tutorial covers building a lightweight, flexible solution from scratch. It won't be nearly as advanced and powerful as the official plug-in. Nevertheless it will help you learn something from jQuery.
- 6) Creating a Slick and Accessible Slide Show Using jQuery
In this in-depth web development tutorial, you’ll learn how to create a usable and web accessible slideshow widget for your site using HTML, CSS, and JavaScript (jQuery) .
- 7) Create a Vertical Scrolling Menu with CSS and jQuery
Create a Vertical Scrolling Menu with CSS and jQuery: With out any hassle of dragging or clicking the scrollbar, users can navigate by just moving the mouse over the content to let it scroll automatically.
- 8) Horizontal Scrolling Menu made with CSS and jQuery
Create a Horizontal Scrolling Menu with CSS and jQuery: With out any hassle of dragging or clicking the scrollbar, users can navigate by just moving the mouse over the content to let it scroll automatically.
- 9) Slide and hide with jQuery
Create simple structure made of a div containing our buttons, we will use some image as buttons, and the section we want to hide/unhide.
- 10) Simple Taps with jQuery
Write less code and create tabs easily with this jQuery plugin.
- 11) how to create a stunning and smooth popup using jQuery
Nowadays, websites are more and more rich and interactive and users are becoming more and more critical with all things in websites. Using windows popup to show important information are in the air and we are going to learn how to create a stunning and great window popup from the scratch using jQuery in a simple and clean tutorial.
- 12) Create a smooth tabbed menu in jQuery
Learn how to create a smooth tabbed menu with our lovely jQuery library. With simple and clean layout we can have a great tabbed menu for this websites.
- 13) How validate forms in both sides using php jQuery
Learn how to validate your forms using PHP and jQuery in both sides: client side (using JavaScript with jQuery) and server side (using PHP) . It will be interesting to see how to use regular expressions to validate different kind of e-mails, passwords and more.
- 14) Improving search boxes with jQuery
Learn how to improve a little more our sites by adding some additional interactions to our search boxes like autofocus, highlighting, and auto replace default text and more by using jQuery.
- 15) Submit a form without page refresh using jQuery
See how easy it is to do just that -- submit a contact form that sends an email, without page refresh using jQuery! (The actual email is sent with a pup script that processes in the background) .
- 16) jQuery tabbed interface tabbed structure menu tutorial
Tabbed Interface or Tabbed Structure Menu is getting really famous in web design & development. This tutorial will show you how to build your own tabbed Interface using jQuery with slideDown/slideUp effect.
- 17) Simple jQuery modal window tutorial
How to create a simple modal window with jQuery. It selects all the anchor tags with name attribute set to "modal" and grab the DIV #id defined in the and displays it as a modal window.18) Tutorial : AJAX interface/menu using jQuery
This tutorial teaches you how to present data using AJAX (using jQuery) with some neat effects. We can use PHP/me to store the data and call it.
- 19) Building modal panels with jQuery
A modal box is a great interface solution when you want to focus the user’s attention to a specific task. It’s ideal for displaying things like alert messages, confirmation dialogues and photos.In this tutorial we’ll build one from scratch using jQuery.
- 20) jQuery-rollovers-using-this
If you’ve been programming in PHP, or other object oriented languages, you may have come across “this” or “self”. With jQuery, we can write $(this) to select an element in the DOM (Document Object Model) . The best way to demonstrate this is with a simple example.
- 21) jQuery image loader
Nice way to load images using jQuery .
- 22) Disjointed Rollovers with jQuery
Learn to put in a rollover effect for the navigation on your web page.
- 23) Inline Image Enlargement with jQuery
Make the image large while hovering without displacing the text.
- 24) Ajaxify you web Pages using jQuery
This simple tutorial will show you how to dynamically load your web content via Ajax instead of default behavior HTTP request (full round trip) .
- 25) PHP Login Form using j
Query
This tutorial shows how to make an Ajax based using jQuery in PHP.
- 26) Building a Light box with jQuery
Create really cool light box with this jQuery tutorial.
- 27) Simple jQuery image slide show with semi transparent caption
How to create a simple image slide show with a semi-transparent caption with jQuery. This example is suitable to display news headlines, or an image slide show in your website FrontPage.
- 28) jQuery image gallery news slider with caption tutorial
A really cool News Slider that uses two strollers to create very slick effect. It uses scroll To to scroll both description and image items and it comes with previous, next, play, stop and mouse over events.
- 29) Create an attractive jQuery menu with fade-in and fadeout effect
We will be learning how to create an attractive menu with more advanced CSS and simple jQuery script. It uses jQuery built-in fade-in and fadeout effect.
- 30) create a vertical horizontal and diagonal sliding content website with jQuery
Create a content sliding website that slide vertically, horizontally or diagonally. This is one of the famous techniques used by most of the portfolio websites.
- 31) Simple lava lamp menu tutorial with jQuery
A little bit of style guide to create a unique lava menu for your own website. It supports styling, different animation transitions and it's so simple.
- 32) jQuery moving tab and sliding content tutorial
Learn how to build a lava lamp tab and sliding content all together with just simple jQuery code. This script is good for sidebar that display recent posts, comments and community news.
- 33) create a stunning sliding door effect with jQuery
Learn how to make a stunning four corners sliding effect easily with jQuery. It's elegant, unique and really cool solution for thumbnail gallery. This tutorial includes detailed explanation that will guide you through the whole process.
- 34) jQuery thumbnail with zooming image and fading caption tutorial
Learn how to build thumbnail gallery with zooming effect and fade-in and fadeout caption. This tutorial will walk you through the concept behind it and how to code it.
- 35) jQuery-tetris
Basic Tetris written in JavaScript and jQuery
- 36) jQuery Menu Roundup
Here is compiled a list of 3 menu plugins, and and 5 ‘custom’ solutions that people have setup.
- 37) Creating Ajax websites based on anchor navigation
Learn how to create an AJAX website without lose the reference to the URL.38) Easy XML Consumption using jQuery
With the popularity of AJAX Web 2.0 style applications and the increase in web services it has become increasingly important to be able to parse XML from the client browser. This is not the easiest thing to do in a cross browser manner without the aid of a JavaScript library that supports XML. Fortunately jQuery makes XML utilization (almost) effortless. If you possess a basic understanding of how to program JavaScript then this tutorial will have you working with XML in 20 minutes
- 39) jQuery Thick box and ColdFusion Dynamic Image Resizing
Build a page which will make use of the Thickbox plug-in, but you don't want need hard code the images. Instead, you'll let ColdFusion scan a folder and create the list for you.
- 40) jQuery/PHP: Simple Random Text Generation Box
Learn how to create a div with a field of text in it, and upon clicking a link, will load a JQuery animation, replace the text inside the box, and then load another jQuery animation.
- 41) how to use jQuery and Ajax.NET Professional together
An example on how to use jQuery and Ajax.NET Professional together.
- 42) jQuery and
- Google Maps Tutorial: #1 Basics
Create a custom
- Google Maps mash up. In this tutorial, you will learn how to get started using jQuery inside the
- Google Maps environment.
- 43) jQuery and
- Google Maps #2: AJAX Storing and Retrieving Point
Learn how to store and retrieve points with using AJAX and a server-side language. This tutorial will use PHP/me on the server, but it is basic enough that re-writing in another language should not be difficult.
- 44) How to find the mouse position with jQuery
Quick tutorial of finding the position of the mouse on a page.
- 45) Really simple live comment preview
Adding a live preview to the comment entry area of WordPress.
- 46) Creating an os web interface in jQuery
Learn how to create the drag & drop interaction, the double click on icons and a basic taskbar with a start disabled button and a real clock of the system.
- 47) How to create a stunning and smooth popup using jQuery
Learn how to create a stunning and great window popup from the scratch using jQuery in a simple and clean tutorial.
- 48) Create an amazing music player using mouse gestures hotkeys in jQuery
Learn how to create an amazing music player coded in xHTML & jQuery that made use of mouse gestures and hotkeys. You can Click & Drag with mouse to interact with interface’s music player or use directional keys & spacebar instead of mouse.
- 49) Animated menus using jQuery
Learn how to create an animated menu (very similar to Dragon Interactive menu) .
- 50) Set hover class for anything
Hovering links and text with CSS is very easy but you cant hover everything with it. This tutorial makes you able to hover everything!
- 51) Characters remaining on an input field
Learn how to create a counter on your input text.
- 52) Text resizing with jQuery
Learn how to allow visitors to inc
rease or decrease the text size (font size) on your website using jQuery.
- 53) Safer Contact Forms Without CAPTCHAs
This tutorial shows how to a build complete, jQuery-based, solution for stopping spammers from miss-using your forms.
- 54) How to load content via Ajax in jQuery
Useful tutorial for those who need to know how to load dynamically some static content in their websites via AJAX.
- 55) Creating Ajax websites based on anchor navigation
Learn how to create an AJAX website without lose the reference to the URL.
- 56) Auto populating select boxes using jQuery Ajax
Allow the user to select a top level category from one select box and to automatically populate the sub-category.
- 57) Auto complete field with jQuery , JSON and PHP
jQuery makes remote scripting a piece of cake and that led me to spend more time coding additional functionalities for the auto-complete field.Learn how to use my auto-complete field.
- 58) Create a stunning sliding door effect with jQuery
Learn how to make a stunning four corners sliding effect easily with jQuery. It's elegant, unique and really cool solution for thumbnail gallery.
- 59) jQuery thumbnail with zooming image and fading caption tutorial
Learn how to build thumbnail gallery with zooming effect and fade-in and fadeout caption. This tutorial will walk you through the concept behind it and how to code it.
- 60) How to use jQuery Date picker plug-in
The jQuery UI Date picker is a highly configurable plug-in that adds date picker functionality to your pages. You can customize the date format and language, restrict the selectable date ranges and add in buttons and other navigation options easily.
- 61) How to use jQuery Week Calendar plug-in
The jQuery-week-calendar plug-in provides a simple and flexible way of including a weekly calendar in your application. It is built on top of jQuery and jQuery up and is inspired by other online weekly calendars such as
- Google calendar.
- 62) jQuery Visualize Plug-in: Accessible Charts & Graphs from Table Elements using HTML 5 Canvas
Learn how to generate bar, line, area, and pie charts from an HTML table, and allows you to configure them in a variety of ways.
- 63) Unit-Testing-with-jQuery-using-Fire Unit-QUnit.aspx
Unit test Java Scripts easily with jQuery
- 64) jQuery UI Dialog w/Resizable iFrame
Resizable Dialog box UI for value added coolness.
- 65) Top 5 jQuery Modal Plug-in
The post has the list of the top 5 jQuery modal Plugging which can be used to either notify or request information to/from the user.
- 66) jQuery Flexigrid Using C#3.0 & LINQ
Flexgrid is a jQuery plug-in!Flexgrig uses jQuery to asynchronously populate content of the grid using either XML or JSON input. This tutorial as the example of using Flexgrid Using C# 3.0 and Line.
- 67) jQuery menu roundup
As jQuery is such a simple language to learn, most people code their own for their own sites. Here is a compiled list of 3 menu plugging, and 5 ‘custom’ solutions that people have setup.
- 68) Formatting your twitter stream with jQuery
Include your twitter stream into your blog or website, and then format it using jQuery so your tweets have an alternating background colour.
- 69) Making a slide in menu using jQuery video tutorial
This tutorial shows how to make a basic slide in/drop down menu using jQuery. The menu itself stylishly slides in and has transparencies so you can view data behind it.
- 70) Building a jQuery-Powered Tag-Cloud
A tag-cloud is a great way of showing visitors to your blog the main topics of interest that are available. There is also additional information contained in a tag-cloud. Aside from the actual links themselves, which give people an idea of the subjects that your site covers, they can also show how popular the different subjects are.Learn how to create Tag-Cloud.
- 71) Create a Photo Admin Site Using PHP and jQuery
Learn hot to create a photo site using PHP, jQuery, and AJAX.
- 72) Use jQuery with
- Google analytics to track clicks on outgoing links from your site
Add outbound link tracking to a new or existing site. Provided that your links to other sites have the REL attribute set, you can track them very easily with some help from jQuery.
- 73) Adding Form validation to WordPress comments using jQuery
When it comes to simpler user experience, having your form validation happen instantly on the same page is a lot cleaner than reloading pages and possibly losing some form content. In this tutorial I'll show you how to use jQuery to do some instant checking on an example comment form.
- 74) Create an apple style menu and improve it via jQuery
Learn how to create extraordinary
- apple style menu.
- 75) Build a Basic Newspaper style layout with WordPress and jQuery
Learn to use the power of jQuery to create a grid layout with size-degrading headers.
- 76) Multiple file upload magic with unobtrusive java script
Magic of jQuery that makes you able to upload multiple files at once. Of course with less code.
- 77) Easy multi select transfer with jQuery
Learn how to select multiple objects from a listbox.
- 78) Rounded Corners with jQuery
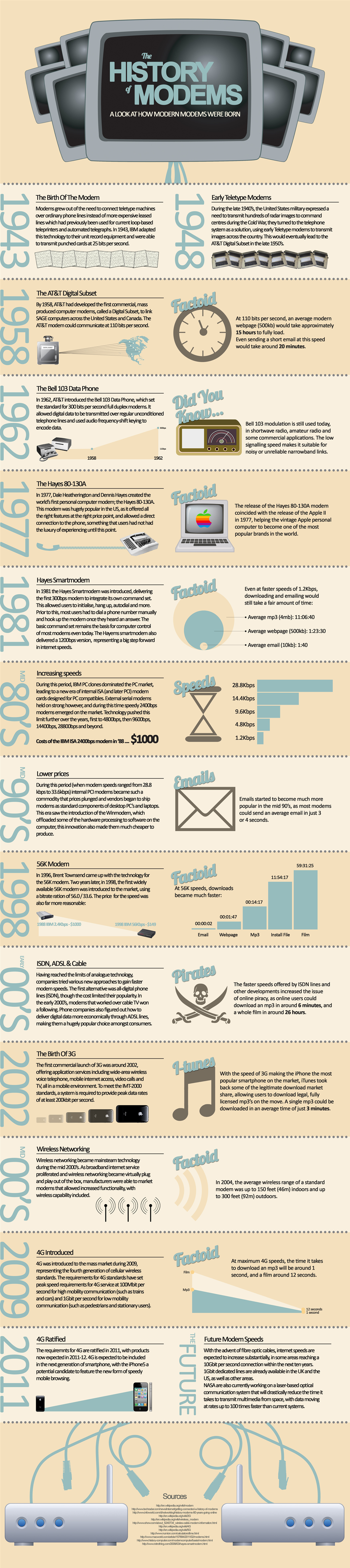
The little boxes we call modems, routers and switches were all born from a need to connect teletype machines together, transferring information started at slow 25 bits per second. At that rate, downloading 1MB might take about 4 days. But we download even full HD movies in real time on ffew hours in on .
ast connections.
JQUERY for Advanced Web Designing
See a Demo of Virtual Panorama
jQuery Tutorials
2. Getting Started with jQuery
3. Multiple File Upload Magic
4. jQuery in 15 minutes
5. jQuery for JavaScript programmers
6. Easy Ajax with jQuery
7. jQuery in 15 minutes
8. jQuery Tutorials for Designers
9. Wrapping Images With A Drop Shadow
10. Simplify Ajax development with jQuery
11. Rounded Corners
12. Getting Around The Minimum Height Glitch
22. Photo Slider Tutorial
23. Text box hints
24. 5 JavaScript Tricks Made Easy with jQuery
25. JQuery Pop-up Menu Tutorial
26. A Quick Code Igniter and JQuery Ajax Tutorial
27. jQuery and XML revisited
28. What is JSONP?
29. Creating A Sliding Image Puzzle Plug-In
30. Slide out and drawer effect
31. Creating accessible charts using canvas and jQuery
32. jQuery liScroll – a jQuery News Ticker
33. Visual jQuery 1.1
jQuery Plugin Directoies
34. Visual jQuery 1.1
35. Plugins | jQuery Plugins
36. jQueryPlugins.com – The Home Of All jQuery Plugins
37.240 jQuery plugins
jQuery Video Tutorials
38. Jquery Smooth Scrolling Tutorial
39. jQuery AJAX forms Tutorial
40. swfupload ajax jquery drupal module image editor
41. jQuery 1.2.3
42. Drag and Drop JQuery + AJAX
43. jComboBox demo Tutorial
jQery Podcasts
44. Drupal Podcast No. 53: Javascript/JQuery in Drupal | Lullabot
45. Podcast 52: Javascript Libraries :: Boagworld
jQuery ebooks
46. jQuery Reference Guide
47. jQuery in Action
jQuery Cheat Sheets
48. Color Charge jQuery Cheat Sheet (PNG Image, 1313×900 pixels)
49. Charlotte web design jQuery Cheat Sheet (pdf)
50. Jquery Cheat Sheet 1.2. (pdf)
Further Reading
51. 50+ Amazing jQuery Examples52. 24 ways: Unobtrusively Mapping Microformats with jQuery